Cybersecurity assessment services use AI agents to scan, score, and secure enterprise systems.
Cybersecurity assessment services refer to AI-driven evaluations that identify vulnerabilities, assess controls, and ensure compliance across digital systems. In Agentic AI environments, autonomous agents run continuous, adaptive assessments to safeguard critical infrastructure and data.
Detailed Definition & Explanation
Cybersecurity assessment services are systematic evaluations of an organization’s cyber posture, risk exposure, and regulatory compliance. Traditionally conducted via periodic audits or static tools, these assessments are now shifting toward autonomous, real-time intelligence powered by agentic AI.
In modern agentic systems:
- Micro-agents ingest logs, access patterns, network telemetry, and endpoint data.
- They correlate indicators of compromise (IOCs) using AI models trained on known threat vectors.
- Agents simulate attacks (e.g., phishing, lateral movement, privilege escalation) in sandboxed environments.
- Through policy-driven reasoning, agents evaluate control effectiveness and flag misconfigurations or exposure zones.
- Outputs are logged in secure, tamper-proof audit trails, feeding downstream governance or remediation workflows.
These assessments may include:
- Penetration testing via simulated attack agents
- Real-time access and identity audits
- Threat modeling with continuously updated risk graphs
- Compliance scans aligned with NIST, ISO 27001, HIPAA, PCI-DSS, and more
As organizations embrace proactive cybersecurity, demand for automated assessment services has surged. According to IDC, only 26% of enterprises scan over 85% of their known IT assets weekly, highlighting a significant need for continuous scanning and vulnerability detection. As cyber threats proliferate, continuous threat exposure management (CTEM) is increasingly critical for cybersecurity teams. According to Gartner, organizations that adopt CTEM—focused on continuous discovery, validation, and remediation—are three times less likely to suffer a breach by 2026.
Why It Matters
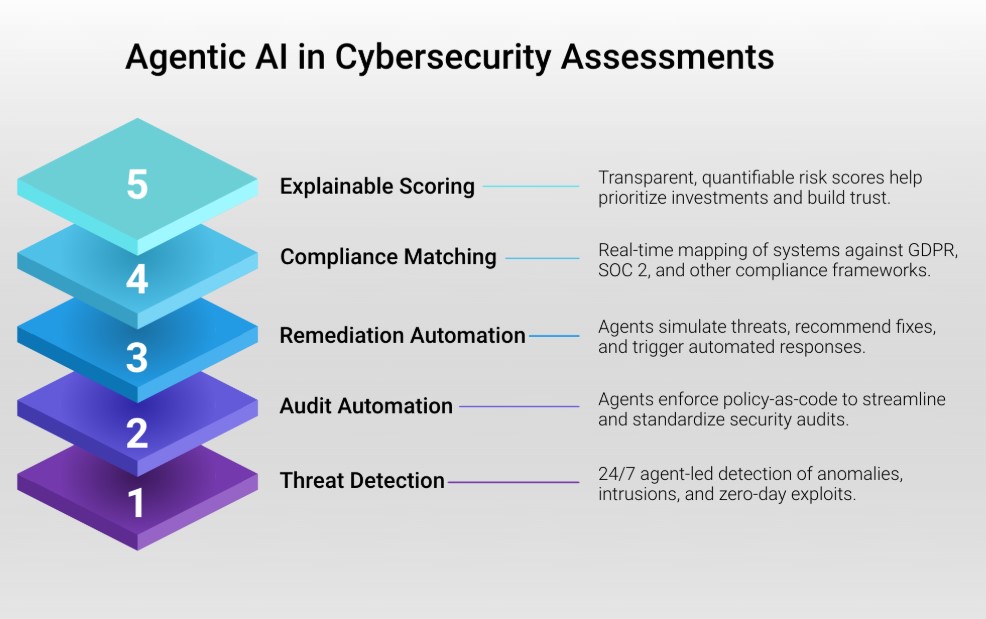
- Enables Continuous Threat Monitoring
Autonomous agents monitor system behavior and anomalies 24/7, identifying threats like credential stuffing or zero-day exploits without manual oversight. This is especially critical in sectors like finance or retail, where minutes of delay can escalate breach impact.
- Reduces Human Error in Audits
Agents automate routine cybersecurity assessments using reproducible policy-as-code logic, ensuring no checklist is missed during audits. In healthcare or manufacturing, this reduces the risk of non-compliance fines and service disruptions.
- Supports Proactive Remediation
Agents can not only flag vulnerabilities but also simulate exploit paths and recommend fixes via change requests or automated patches. For example, in enterprise IT, agents may disable unused ports, enforce MFA, or push firmware updates autonomously.
- Accelerates Compliance Readiness
Assessment agents interpret compliance frameworks like GDPR or SOC 2 and match real-time infrastructure states against them. In SaaS businesses, this drastically reduces the time required for audit preparation and documentation.
- Provides Explainable Risk Scores
Using explainable AI models, agents assign quantifiable risk scores to systems, workflows, or user behaviors, helping CISOs prioritize investment. In education and public services, this democratizes security visibility for non-technical stakeholders.
Real-World Examples
Palo Alto Networks – Cortex Xpanse
An agent-based attack surface management platform that continuously scans external infrastructure for misconfigurations, shadow IT, and exposed services. It autonomously identifies high-risk assets and suggests prioritized remediation.
IBM Security – QRadar Suite
Utilizes AI agents for behavior analytics, vulnerability scanning, and real-time threat detection. It helps organizations streamline cyber risk assessment and compliance across hybrid cloud environments.
FD Ryze – Cyber Assessment Agents
FD Ryze enables cybersecurity assessments through agentic orchestration. Its agents scan access logs, simulate phishing payloads, flag policy violations, and create SOC-ready reports, thereby empowering teams to maintain a proactive security posture without constant human intervention.
What Lies Ahead
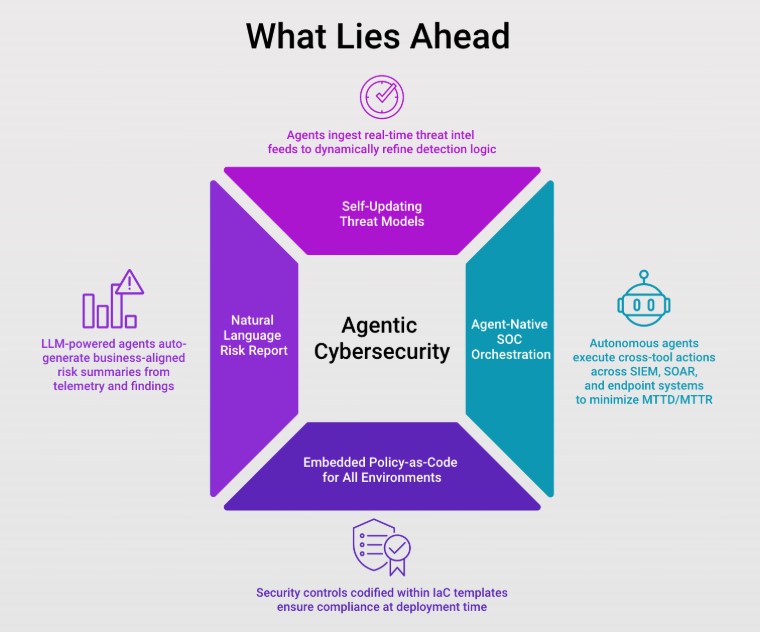
- Self-Updating Threat Models
Assessment agents will incorporate real-time threat intelligence feeds and update their detection logic without human input, ensuring relevance in a fast-evolving landscape.
- Agent-Native SOC Orchestration
Cybersecurity agents will coordinate autonomously with SOC tools like SIEMs, firewalls, and incident response platforms to reduce mean time to detect/respond (MTTD/MTTR).
- Embedded Policy-as-Code for All Environments
Assessment logic will be embedded into infrastructure-as-code templates, enabling security to be enforced and assessed during every deployment cycle.
- Natural Language Risk Reports
Agents will generate stakeholder-facing reports in plain language, mapping technical risks to business outcomes and streamlining communication for boards, auditors, and partners.
Related Terms
- Threat Modeling
- Vulnerability Scanning
- Compliance Automation
- Zero-Trust Architecture
- AI-Driven Penetration Testing
- Policy-as-Code
- Attack Surface Management
- SOC Automation
- Real-Time Cyber Risk Scoring
